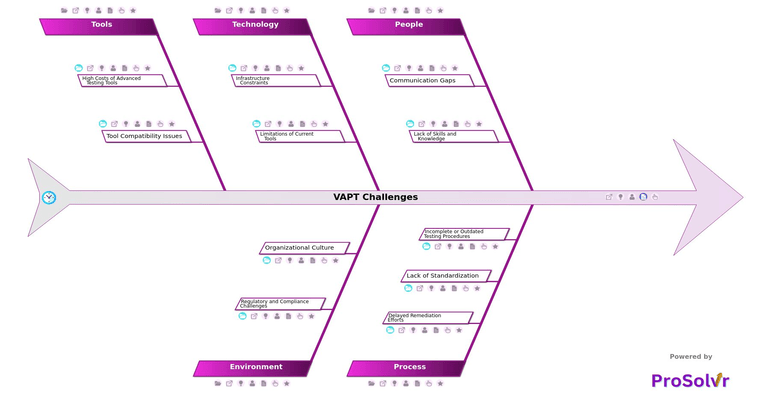
RCA of VAPT Challenges
Vulnerability Assessment and Penetration Testing (VAPT) is a critical component of a cybersecurity strategy, designed to identify and mitigate potential security weaknesses before they can be exploited. However, conducting VAPT effectively is fraught with challenges that can undermine its effectiveness. One major issue is the lack of standardization in processes, such as inconsistent risk scoring criteria and variation in testing methods across teams, which can lead to fragmented or incomplete assessments. Additionally, infrastructure constraints such as outdated systems and legacy technology or limited resources for comprehensive testing can prevent organizations from conducting deep, system-wide evaluations. These technical limitations are compounded by communication gaps and inconsistent reporting of findings, which make it difficult to translate assessment results into actionable remediation steps.
When VAPT is not conducted thoroughly or interpreted correctly, it can lead to serious problems in cybersecurity. For instance, miscommunication of remediation efforts may result in vulnerabilities remaining unpatched, and poor coordination with IT teams for fixes often delays resolution timelines. Moreover, overlooking certain vulnerability types due to incomplete or outdated testing procedures increases the risk of breaches. In environments where budget constraints limit access to advanced tools or skilled personnel, even identified risks may not be mitigated effectively. These issues collectively weaken the security posture, leaving systems exposed and compliance at risk.
This is where GEN-AI powered root cause analysis using a fishbone diagram grounded in Six Sigma principles becomes valuable. After a security incident has occurred, such a structured approach helps organizations identify not just what failed, but why it failed. The fishbone diagram systematically categorizes possible causes under major heads, allowing teams to visually map out all contributing factors. For example, if an exploit was successful due to low detection accuracy in complex environments, a root cause analysis might trace it back to the limitations of current tools and lack of integration with other security platforms. This insight provides the basis for not only fixing the current issue but also implementing process improvements to prevent recurrence.
An AI-powered application like ProSolvr, which incorporates fishbone diagrams, enhances this analytical process by enabling collaborative, structured analysis of incidents. It can guide teams through the root cause identification process using Six Sigma framework. In doing so, it facilitates the development of effective Corrective and Preventive Actions (CAPA) by organizations.
Leveraging AI-driven root cause analysis tools post-incident empowers organizations to shift from reactive firefighting to proactive improvement. By identifying the deeper systemic issues—such as inadequate training programs, conflicts between security and IT tools, or penalties for non-compliance creating rush in testing—organizations can establish long-term solutions that enhance both their resilience and regulatory alignment.
Who can learn from the VAPT Challenges template?
- Cybersecurity Teams: These professionals directly handle threat detection, prevention, and mitigation. RCA helps them understand underlying weaknesses such as low detection accuracy or lack of integration with other security platforms, enabling more robust defenses.
- IT and Infrastructure Teams: Since they are responsible for system maintenance and implementation of fixes, RCA findings—like poor coordination with IT teams for fixes or outdated systems and legacy technology—highlight areas for improvement in collaboration and infrastructure planning.
- Developers and DevOps Teams: These teams often need to implement security recommendations. Learning from RCAs helps address issues such as misalignment between security teams and developers and promotes secure coding practices.
- Risk and Compliance Officers: RCA offers valuable insights into systemic issues like frequent updates to compliance requirements or variation in testing methods, helping them ensure adherence to security and regulatory standards.
- Executive Leadership and Management: Understanding root causes like budget constraints on security initiatives or lack of emphasis on security in development cycle can inform better strategic decisions, resource allocation, and organizational prioritization of cybersecurity.
- Training and HR Teams: By learning that inadequate training programs or lack of skills and knowledge are root causes, HR and training teams can design more targeted upskilling initiatives to close knowledge gaps and build a more security-aware workforce.
Why use this template?
Leveraging AI-driven root cause analysis tools post-incident empowers organizations to shift from reactive firefighting to proactive improvement. By identifying the deeper systemic issues—such as inadequate training programs, conflicts between security and IT tools, or penalties for non-compliance creating rush in testing—organizations can establish long-term solutions that enhance both their resilience and regulatory alignment.
Use ProSolvr by smartQED to address cybersecurity breaches in your organization, effectively and efficiently.