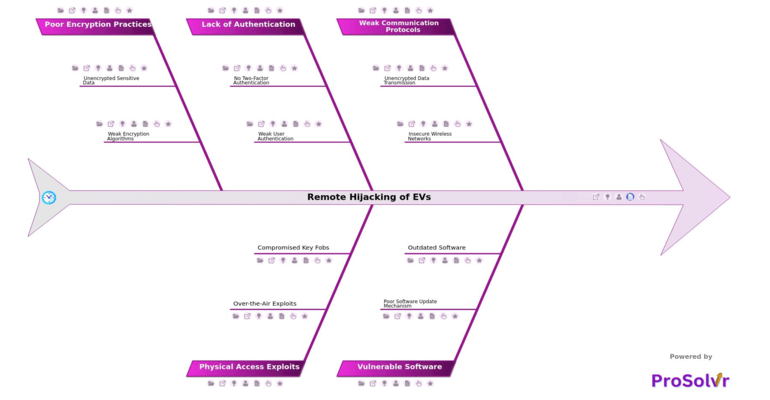
RCA of Remote Hijacking of EVs
Remote hijacking of electric vehicles (EVs) refers to unauthorized access and control of an EV's systems via network vulnerabilities. Modern EVs are equipped with a variety of connected components, from GPS and Bluetooth to Wi-Fi and cellular connections, making them susceptible to cyber attacks. These connections enable features like over-the-air software updates and real-time diagnostics, but they can also serve as entry points for attackers.
Hackers who gain access remotely may manipulate critical functions, such as steering, braking, and acceleration, posing serious safety risks to passengers and the public. Remote hijacking can compromise not only vehicle safety but also sensitive driver data, making it a significant cybersecurity threat. Vulnerabilities in the software or network architecture of EVs could be exploited to breach networks at large, affecting multiple EVs from a central point. This raises concerns for individuals, manufacturers, and even national security.
Root Cause Analysis (RCA) using an application like ProSolvr, offers a structured approach to identifying and addressing the underlying causes of remote hijacking vulnerabilities in EVs. This methodical approach helps stakeholders to develop effective corrective and preventive actions, reducing the likelihood of similar issues arising in the future. RCA helps streamline communication across departments, ensuring a collaborative approach to resolving security flaws in a comprehensive and sustainable manner.
Who can learn from the Remote Hijacking of EVs template?
- Automotive Cybersecurity Engineers: These professionals work on securing the software and hardware of EVs, focusing on implementing protocols that prevent unauthorized access. The template would guide them in identifying weak points and developing solutions.
- Vehicle Manufacturers and Designers: The template would help automotive companies’ R&D teams ensure their designs prioritize cybersecurity, integrating preventive measures early in the vehicle design and manufacturing process.
- Information Technology (IT) Security Teams: These teams monitor and manage the cybersecurity aspects of connected infrastructure. The template would provide a structured approach to proactively safeguard vehicle software and networks.
- Regulatory Bodies and Standards Organizations: Organizations that create and enforce cybersecurity regulations for automotive safety could use this template to outline standardized security practices and ensure compliance across the industry.
- Risk Assessment and Compliance Officers: These individuals assess potential vulnerabilities and ensure compliance with regulatory standards. The template would serve as a valuable tool for conducting risk assessments and implementing best practices.
- Cybersecurity Consultants and Auditors: External consultants and auditors specializing in vehicle cybersecurity can use the template to evaluate EVs for vulnerabilities, offering recommendations and auditing security measures to mitigate risks effectively.
Why use this template?
The use of Generative AI (Gen AI) in Root Cause Analysis (RCA) with a fishbone diagram can be instrumental for diagnosing and preventing remote hijacking of EVs. A GEN-AI powered application like ProSolvr can analyze vast amounts of public data to identify potential causes, assisting cybersecurity teams in pinpointing issues across software, hardware, and communication systems. By visualizing these problem areas in a fishbone diagram, teams can systematically tackle each root cause, making targeted improvements that strengthen EV cybersecurity defenses.
Use ProSolvr by smartQED in your organization to bolster EV security and stay ahead of cyber threats.