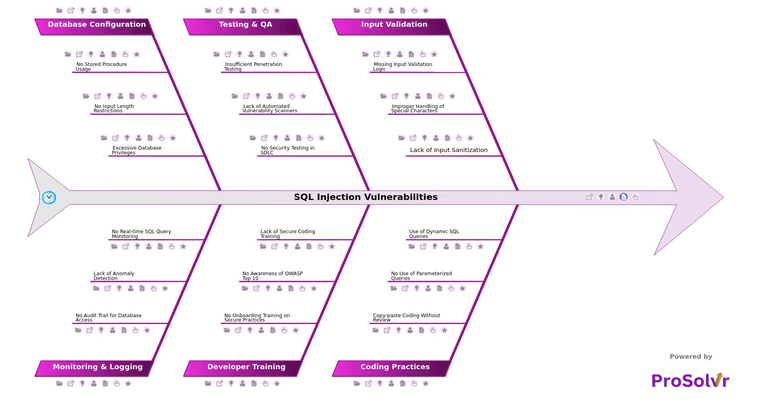
RCA of SQL Injection Vulnerabilities
SQL Injection Vulnerabilities occur when an application fails to properly validate or sanitize user inputs before passing them to a database query. Attackers exploit this weakness by inserting malicious SQL statements into input fields, URLs, or API parameters, manipulating the database to reveal sensitive data, modify records, or even gain administrative access. This type of attack is one of the oldest and most dangerous in cybersecurity because it directly targets the heart of an organization’s data infrastructure. A single successful injection can compromise entire databases, leading to data breaches, financial loss, and severe reputational damage.
When input validation mechanisms are weak, attackers can easily bypass security barriers. Poor coding Practices like copying and pasting code without review or the use of dynamic SQL queries make the system more prone to injection flaws. Inadequate testing & QA processes, such as insufficient penetration testing or the lack of automated vulnerability scanners, further amplify these risks by allowing vulnerabilities to remain undiscovered. The result is a chain of systemic weaknesses that together open pathways for exploitation and long-term cybersecurity threats.
After an incident like a SQL injection attack has occurred, performing a thorough Root Cause Analysis (RCA) becomes essential. A GEN-AI powered RCA, supported by a fishbone diagram and grounded in Six Sigma principles, helps teams visualize how various contributed to the event.
A dedicated root cause analysis application like ProSolvr, which integrates fishbone diagrams with GEN-AI and Six Sigma methodologies, can be a game-changer for cybersecurity teams. This structured approach not only identifies the underlying causes but also helps organizations develop effective Corrective, Preventive, and Investigative Actions (CAPA) to ensure such vulnerabilities are permanently mitigated.
Who can learn from the SQL Injection Vulnerabilities template?
- Quality Assurance (QA) Teams: QA professionals can learn about gaps in input validation, coding practices, and testing processes, helping them strengthen security testing and ensure compliance with secure development standards.
- Development Teams: Developers can understand how poor coding practices, lack of parameterized queries, and insufficient secure coding training contribute to SQL injection vulnerabilities, enabling them to improve code quality and adopt safer development practices.
- Database Administrators (DBAs): DBAs can gain insights into issues like excessive database privileges, lack of stored procedure usage, and improper input length restrictions, helping them implement tighter database security controls.
- Cybersecurity and Risk Management Teams: These teams can use the RCA to identify systemic vulnerabilities, understand attack pathways, and design preventive measures to reduce the likelihood of future SQL injection attacks.
- Training and HR Departments: By reviewing the RCA, training teams can identify gaps in onboarding and secure coding training, allowing them to develop targeted programs to improve developer awareness and skills.
- Testing & QA Managers: Managers responsible for testing can learn about deficiencies in penetration testing, automated vulnerability scanning, and SDLC security checks, helping them implement more robust testing protocols and oversight processes.
Why use this template?
ProSolvr helps visualize interdependencies between causes, highlight procedural and technical gaps, and generate well-structured CAPA strategies. ProSolvr helps organizations detect what may seem like isolated errors and turn them into actionable insights. It can guide teams toward sustainable process improvements and stronger defense mechanisms against future cyberattacks.
Use ProSolvr by smartQED for successfully mitigating cybersecurity issues and safeguarding valuable data in your organization.