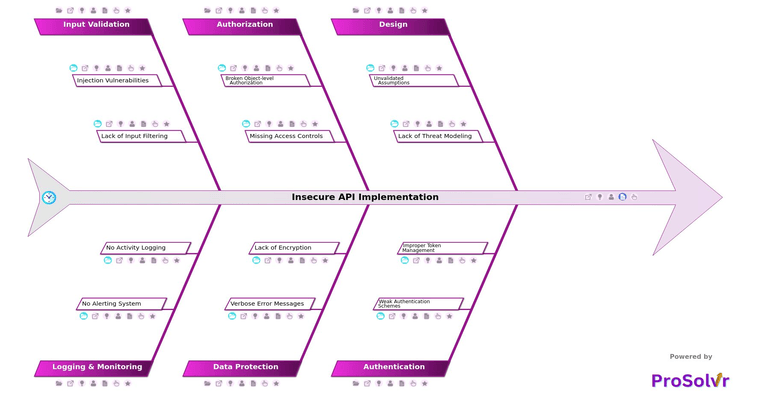
RCA of Insecure API Implementation
Insecure API Implementation happens when APIs are not protected properly. APIs help systems share data and connect different applications. If they are designed or used without strong security, they become serious API vulnerabilities. Common design problems include missing input checks, trusting unsafe data, and not planning for security threats. Without threat modeling or risk analysis, teams cannot see possible attack surfaces or understand how hackers might break in.
Weak authentication is one of the biggest risks in API security. Many APIs still use basic login methods or skip multi-factor authentication. This allows attackers to act like real users and steal information. Poor authorization creates more danger. When access rules are missing, users can view or change data that should be private. Without proper role-based or rule-based controls, sensitive information can leak and cause major data breaches.
APIs must also protect data at every step. If data is sent without encryption or stored in plain text, attackers can read it easily. Detailed error messages or system logs can reveal how your system works, making attacks easier. Poor input filtering leads to SQL Injection or Command Injection attacks that damage databases or expose user data. Following OWASP API Security Risks can help reduce these issues and prevent API data leaks.
Many breaches go unnoticed because there is no logging, alerting, or monitoring. Without audit trails or real-time alerts, teams find problems too late. ProSolvr helps organizations fix insecure APIs using AI tools for Root Cause Analysis. It gives teams a clear visual map of causes through an interactive fishbone view, making it easy to see how design, authentication, authorization, data protection, and monitoring connect to the issue. Using Six Sigma-based corrective actions and CAPA tracking, ProSolvr helps enterprises fix the real cause and build stronger, safer APIs for the future.
Who can learn from the Insecure API Implementation template?
- Cybersecurity Teams: They can learn how insecure API implementations expose systems to vulnerabilities and use RCA findings to strengthen authentication, authorization, and data protection practices.
- Software Development Teams: Developers can understand how design flaws like unvalidated assumptions or missing input validation contribute to breaches and apply preventive controls in future API designs.
- Quality Assurance (QA) Engineers: QA professionals can use RCA insights to identify recurring security testing gaps, improve validation coverage, and ensure robust pre-deployment checks.
- Risk and Compliance Officers: They can leverage the structured RCA outcomes to ensure corrective and preventive actions meet cybersecurity compliance standards and audit requirements.
- IT Operations and Infrastructure Teams: These teams can learn how weaknesses in monitoring and logging affect incident detection and apply CAPA to enhance system visibility and response.
- Training and Security Awareness Teams: They can use RCA results to design targeted training programs addressing issues like weak authentication schemes and improper token management.
Why use this template?
ProSolvr makes Root Cause Analysis simple and effective. It turns a manual process into a structured, intelligent workflow. Teams can clearly see how technical failures relate to design and process weaknesses.
Once root causes are identified, organizations can take targeted Corrective and Preventive Actions (CAPA) to fix security gaps and prevent future API vulnerabilities.
With ProSolvr by smartQED teams can strengthen API security, close system gaps, and protect critical data before breaches happen.