RCA of Insecure Direct Object Reference
Insecure Direct Object Reference (IDOR) is a common and serious web security vulnerability. It happens when an app exposes internal data or files directly through a URL or API, without proper access control. For example, changing a user ID in a URL like /user?id=101 to /user?id=102 may show another person’s data. This happens because the system does not check permissions correctly. IDOR vulnerabilities are part of the OWASP Top 10 and are often found during Vulnerability Assessment and Penetration Testing (VAPT).
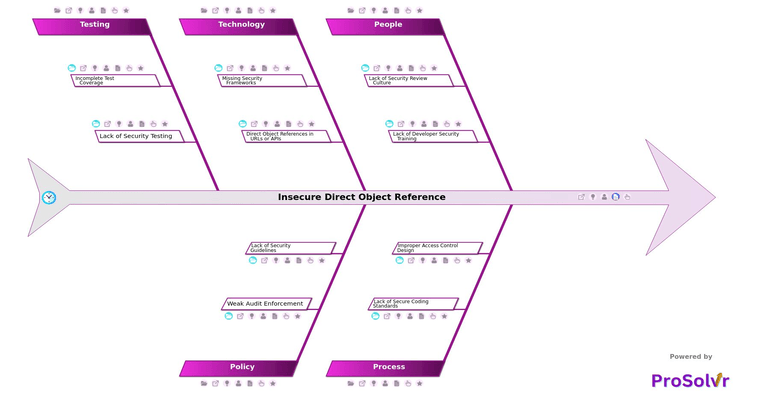
To truly fix IDOR issues, teams must look deeper, not just at the code but at the reasons behind it. A root cause analysis using a fishbone diagram helps uncover those reasons. Under People, the causes may include a Lack of Security Review Culture, Security not integrated into SDLC, No peer review for security flaws, and Lack of Developer Security Training. Under Process, the team may have No centralized access control mechanism or No secure design review. In Technology, developers might use Direct Object References in URLs or APIs, Exposing predictable IDs, or miss using Role-Based (RBAC) or Attribute-Based Access Control (ABAC) frameworks. Policy and Testing issues, such as Weak audit enforcement, No test cases for ID manipulation, and Penetration testing not conducted — also add to the risk.
A platform like ProSolvr makes this analysis simple and visual. It allows teams to build AI-powered fishbone diagrams that map all possible causes under People, Process, Technology, Policy, and Testing. ProSolvr also helps in assigning and tracking Corrective and Preventive Actions (CAPA) so that problems are fixed at their roots. Teams can work together, document insights, and ensure that security gaps are not repeated in future releases.
To prevent Insecure Direct Object Reference (IDOR) from occurring again, organizations should follow clear security steps: use centralized access control, hide or randomize object IDs, adopt secure coding standards, and make security testing a part of every release. When combined with structured analysis through ProSolvr, these actions build a stronger security culture and protect applications from repeat vulnerabilities.
Who can learn from the Insecure Direct Object Reference template?
- Software Developers: Developers can learn how insecure coding and assumptions about user behavior can lead to serious risks like IDOR. The RCA shows why it’s important to build security into every line of code and ensure proper authorization checks.
- Security Architects and Engineers: They can identify design flaws such as missing access controls or predictable object references. The RCA helps them design safer systems with stronger and smarter access rules.
- Quality Assurance (QA) and Testing Teams: The RCA points out common testing gaps like skipping authorization tests or missing ID manipulation cases. QA teams can use this to include security checks in test plans and use tools for automated validation.
- Project Managers and SDLC Coordinators: They can see how weak processes and missing peer reviews cause security lapses. The RCA encourages them to build stronger checkpoints for security at every stage of development.
- Policy Makers and Compliance Officers: The RCA explains how weak audit policies allow issues to stay hidden. These insights help in updating access control policies and improving compliance with standards like OWASP.
- Cybersecurity Trainers and Educators: Trainers can use RCA findings as real-world lessons to teach how IDOR happens and how it can be prevented through better coding and testing practices.
Why use this template?
Fixing an IDOR issue is not just about changing a few lines of code, it’s about fixing the system that caused it. Using ProSolvr, powered by Gen-AI and Six Sigma principles, teams can dig deeper into the real causes, learn from them, and build lasting security habits. It helps organizations not only resolve vulnerabilities but also strengthen their overall security culture.
Use ProSolvr by smartQED to quickly and effectively solve problems, learn from incidents, and build a more secure and resilient development process.