RCA of Persistent Malware Infections
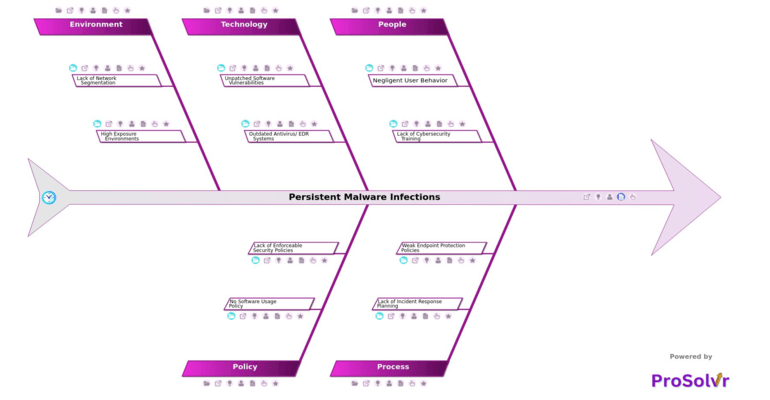
Persistent malware infections represent a significant threat in the cybersecurity landscape, characterized by their ability to maintain a foothold within systems despite standard detection and remediation efforts. These infections are often designed to survive reboots, avoid detection, and reinitiate malicious activity over time. The implications are severe: continuous data breaches, operational disruption, compromised system integrity, and erosion of stakeholder trust. The stealthy and enduring nature of such malware often exposes underlying vulnerabilities across technical, procedural, and human dimensions within an organization.
A structured root cause analysis becomes essential to understanding how and why the infection persisted. A GEN-AI powered root cause analysis using a fishbone (Ishikawa) diagram structured on Six Sigma principles can play a critical role in this phase. This approach helps teams systematically dissect the problem into contributing categories, thereby identifying latent issues that allowed the malware to proliferate. Unlike real-time diagnostics, this retrospective analysis focuses on learning from the incident, enabling organizations to create effective Corrective and Preventive Actions (CAPA). By eliminating root causes rather than just symptoms, it minimizes recurrence and builds long-term resilience.
For example, under the People category, causes like negligent user behavior including ignoring update prompts or downloading software from untrusted sources highlight gaps in user practices. The Process dimension might expose lack of incident response planning, where delayed response to alerts and no containment procedures allowed the malware to spread unchecked. The Technology branch may reveal unpatched software vulnerabilities such as applications not patched and OS not updated, which are commonly exploited by persistent threats. These interconnected causes demonstrate the multifaceted nature of such incidents and the need for a comprehensive analytical approach.
Applications like ProSolvr, which utilize fishbone diagrams to guide root cause analysis, can significantly enhance problem solving. ProSolvr enables teams to visually map out and categorize causes in a collaborative interface, promoting clarity and alignment.
Who can learn from the Persistent Malware Infections template?
- IT and Cybersecurity Teams: These professionals can gain insights into system vulnerabilities, response inefficiencies, and areas where technical defenses failed, allowing them to enhance their threat detection and mitigation strategies.
- Management and Leadership: Understanding the RCA helps decision-makers recognize organizational weaknesses, allocate resources effectively, and prioritize cybersecurity investments and policy improvements.
- Compliance and Risk Officers: This group can use the findings to assess regulatory gaps, ensure alignment with industry standards, and implement risk reduction measures that strengthen overall governance.
- End Users and Employees: RCA outcomes can inform awareness training, helping users understand the consequences of unsafe practices and encouraging more secure behavior in daily operations.
- Incident Response and Crisis Management Teams: By studying the timeline and breakdown of the response effort, these teams can refine their protocols, improve coordination, and better prepare for future incidents.
- Software and System Administrators: These individuals can learn how to implement more robust configuration management, patching routines, and system hardening practices based on the breakdowns observed during the infection.
Why use this template?
Leveraging a disciplined root cause analysis process supported by intelligent tools like ProSolvr ensures not only effective response but also organizational learning. It transforms a reactive posture into a proactive one, ensuring that each incident becomes a catalyst for systemic improvement. Once root causes are identified, ProSolvr facilitates organization in the documentation and tracking of CAPA initiatives ensuring that corrective measures such as enhanced training, updated software policies, or network segmentation practices are implemented and monitored effectively.
Use ProSolvr by smartQED to effectively resolve problems in your organization.