RCA of Frequent Account Compromises
Frequent account compromises occur when unauthorized individuals gain repeated access to user accounts within an organization. These incidents are a serious cybersecurity concern, often caused by phishing, poor password hygiene, or technical vulnerabilities. Once credentials are compromised, attackers can move laterally through systems, exposing sensitive data and disrupting business operations. Beyond operational risk, these events often result in reputational damage, financial losses, and compliance violations. What makes the problem more dangerous is its recurring nature, driven by unresolved root causes.
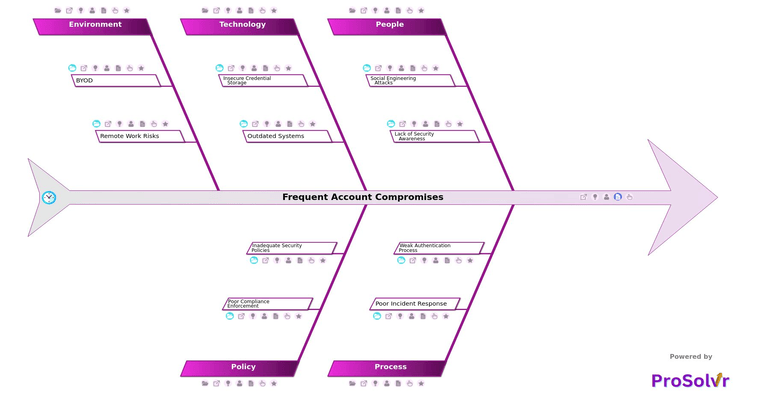
These incidents are rarely isolated. They arise from a combination of human behavior, process weaknesses, outdated technologies, flawed policies, and environmental risks. Employees may fall victim to phishing due to a lack of phishing simulations, limited security awareness, password reuse, or the absence of regular training. On the process side, delayed detection, no root cause analysis after incidents, weak authentication flows, and the lack of multi-factor authentication create exploitable gaps. Technological issues like plaintext passwords, weak hashing algorithms, unsupported authentication mechanisms, outdated systems, and unpatched vulnerabilities lower the organization’s defenses. Policy-level failures, such as poor compliance enforcement, inadequate security policies, no password complexity requirements, and lack of accountability, further exacerbate the threat. The remote work environment introduces additional risks such as unsecured home networks, shared devices, no mobile device management, and uncontrolled access points.
To effectively respond to such recurring threats, organizations must adopt a structured post-incident Root Cause Analysis approach. This is where ProSolvr provides significant value. Designed for post-event investigation rather than real-time detection or diagnosis, ProSolvr enables security and IT teams to analyze incidents using AI-assisted fishbone diagrams and Six Sigma principles. The platform helps categorize and visualize contributing factors across people, processes, technology, policy, and environment. By supporting teams in identifying true root causes and developing strong Corrective and Preventive Actions, ProSolvr transforms complex incidents into clear, actionable insights that strengthen long-term security and operational resilience.
Who can learn from the Frequent Account Compromises template?
- IT Security Teams: IT security teams benefit directly from root cause insights, helping them identify overlooked technical vulnerabilities and implement stronger defenses against account takeovers.
- Training and Awareness Coordinators: Training and awareness coordinators gain a deeper understanding of human behavior and social engineering tactics. This enables them to design more impactful training programs and phishing simulations tailored to actual root causes.
- Policy Makers and Compliance Officers: Policy makers and compliance officers can use RCA findings to reinforce governance frameworks, improve accountability mechanisms, and close policy-level gaps that contribute to recurring breaches.
- Incident Response and Risk Management Teams: Incident Response and Risk Management teams refine their response protocols and post-incident workflows by learning what failed and why. This results in more robust containment and mitigation strategies.
- System Administrators and DevOps Engineers: System administrators and DevOps engineers, often responsible for configurations and infrastructure, can address the technical root causes highlighted in the RCA to harden systems and eliminate recurring weak points.
- Executive Leadership and Business Managers: Executive leadership and business managers may not handle technical details, but they benefit from understanding the business impact of frequent compromises. RCA results give them clear visibility into risk exposure and help justify investments in cybersecurity tools, employee training, and policy enhancements.
Why use this template?
The Frequent Account Compromises template in ProSolvr helps teams visually map complex incident scenarios, linking root causes to actual breaches across people, process, technology, policy, and environment. By simplifying the visualization of cause-effect relationships and surfacing actionable CAPA (Corrective and Preventive Actions), ProSolvr ensures teams move beyond surface-level fixes toward focused, strategic remediation.
Unlike diagnostic or real-time monitoring tools, ProSolvr is purpose-built for post-incident analysis. Its AI-powered RCA framework, based on fishbone diagrams and Six Sigma principles, enables teams to identify and organize deep-rooted issues, apply meaningful corrective measures, and prevent recurrence. This not only resolves current vulnerabilities but also helps build a stronger, more resilient cybersecurity posture over time.
Use ProSolvr by smartQED to investigate and resolve cybersecurity challenges more effectively backed by community insights and real-world examples.