RCA of Phishing Attacks
Phishing attacks in cybersecurity involve tricking individuals into providing sensitive information, such as passwords, financial details, or personal data, by disguising malicious communications as legitimate. These attacks often occur through emails, messages, or fake websites designed to look trustworthy. Phishing can lead to identity theft, financial losses, and unauthorized access to networks, making it a significant threat to both individuals and organizations.
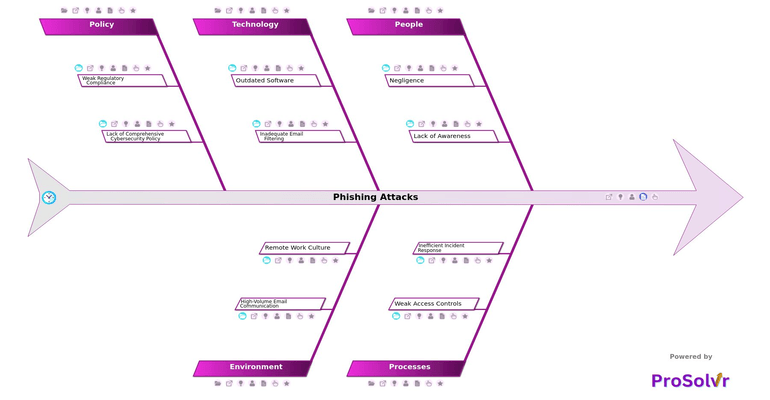
Using a fishbone diagram, also known as an Ishikawa diagram, to perform root cause analysis can help break down the complex factors contributing to phishing attacks. By categorizing the potential causes into key areas like human error, inadequate security training, or poor email filtering systems, the diagram visually organizes contributing factors. This structured approach allows teams to focus on the root causes rather than symptoms, leading to more effective solutions.
Root cause analysis (RCA) with an application like ProSolvr can help identify the underlying reasons behind phishing attacks, such as gaps in security training or inadequate email filtering. By pinpointing these root causes, organizations can develop targeted corrective actions, like enhanced security protocols and employee awareness programs. The structured approach ensures that corrective and preventive actions (CAPA) directly address the specific weaknesses identified. This leads to more sustainable improvements in overall cybersecurity defenses.
Who can learn from the Phishing Attacks template?
- IT Security Teams: They can use the template to enhance cybersecurity protocols and implement effective preventive measures against phishing attacks.
- Management and Leadership: Executives and decision-makers can learn how to support cybersecurity initiatives, allocate resources, and enforce policies to mitigate phishing risks.
- Employees and End-Users: General staff can benefit from the template by understanding how to recognize phishing attempts and follow best practices to avoid them.
- Compliance Officers: They can use the information to ensure the organization meets legal and regulatory requirements for cybersecurity and data protection.
- Risk Management Teams: These teams can integrate the findings from the cybersecurity template into broader risk assessments, ensuring phishing risks are minimized across the organization.
Why use this template?
ProSolvr's Generative AI (Gen AI) can enhance root cause analysis (RCA) by quickly processing and analyzing vast amounts of information related to phishing incidents, identifying patterns and root causes more efficiently. It can help automate the categorization of phishing attack factors, such as weak security protocols or human errors, and organizations can implement tailored corrective and preventive actions accordingly. By identifying potential phishing scenarios and providing insights on vulnerabilities, a GEN-AI powered quality application like ProSolvr, can help organizations strengthen their phishing detection systems. It can also help organizations proactively address gaps in their cybersecurity measures, reducing the likelihood of future attacks.
Enhance your company's defenses against phishing attacks— use ProSolvr by smartQED for proactive, tailored cybersecurity solutions today!