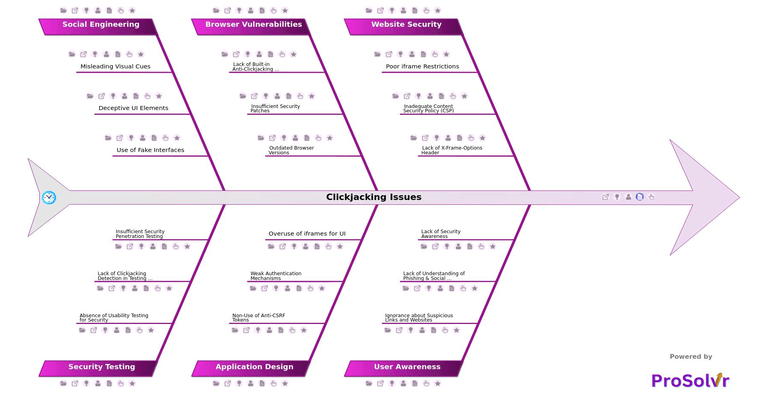
RCA of Clickjacking Issues
Clickjacking is a malicious cybersecurity technique where attackers deceive users into clicking on elements that are hidden or disguised. Typically, this is done by overlaying a transparent or misleading button over a legitimate webpage, causing users to unknowingly interact with hidden content. For instance, users may believe they are clicking to play a video but instead approve a transaction or share sensitive information. This manipulation takes advantage of a user’s trust in a website and can lead to serious cybersecurity breaches.
In terms of impact, clickjacking can result in unauthorized transactions, session hijacking, and exposure of sensitive data. Attackers often exploit vulnerabilities in websites that lack proper security measures such as frame-busting techniques or Content Security Policies (CSP). With the increasing reliance on e-commerce and online banking, the risks associated with clickjacking have escalated, making it crucial for organizations to strengthen their defenses and protect user data.
To tackle this issue, organizations can leverage Root Cause Analysis (RCA). By utilizing RCA techniques like the fishbone diagram, teams can systematically investigate the factors contributing to clickjacking vulnerabilities. Common causes might include flaws in web application design, inadequate security policies, lack of employee training, or misconfigurations in server settings. Through this structured analysis, organizations can develop corrective actions such as implementing anti-clickjacking defenses, improving security protocols, and conducting regular audits of web applications.
By addressing these root causes, organizations can mitigate the risk of clickjacking and enhance their overall cybersecurity posture. The use of Root Cause Analysis helps ensure that vulnerabilities are not only identified but also effectively resolved, reducing the likelihood of future attacks.
Who can learn from the Clickjacking Issues template?
- Web Developers: Developers can use the fishbone analysis to understand the technical vulnerabilities, such as improper use of security headers (e.g., X-Frame-Options), and implement more robust coding practices to prevent clickjacking attacks.
- Cybersecurity Teams: Security analysts and engineers can identify the root causes of clickjacking vulnerabilities across web applications, helping them enhance overall security measures, monitor for suspicious activity, and prevent such attacks.
- IT Managers: IT management can gain insights into the procedural gaps or misconfigurations within systems and web servers. This can inform their decision-making about security protocols and resource allocation for improving defenses against clickjacking.
- Quality Assurance (QA) Teams: QA testers can use the fishbone diagram to structure their security testing and validation processes. This will help them assess whether the web applications adhere to security best practices that mitigate clickjacking risks before release.
- Compliance and Audit Professionals: These professionals can use the fishbone template to evaluate how well the organization adheres to security standards, industry regulations, and compliance requirements concerning web security and user data protection.
- Educators and Trainers: Instructors involved in cybersecurity education can use the fishbone diagram as a teaching tool to illustrate how clickjacking works and the variety of factors that can contribute to such vulnerabilities, providing a holistic learning experience for students or trainees.
Why use this template?
Using Generative AI (Gen-AI) for clickjacking root cause analysis offers several key benefits. It can quickly analyze large amounts of data from public domains to identify patterns or vulnerabilities that might be overlooked by human analysts. Additionally, using a Gen-AI visual tool like ProSolvr can help streamline the creation of detailed fishbone diagrams by automating the categorization of potential causes. This makes the analysis process more efficient and comprehensive. This helps organizations address the root causes of clickjacking faster and with greater accuracy, improving overall security.
Use ProSolvr by smartQED to efficiently identify and resolve cybersecurity issues in your organization.