RCA of Distributed Denial of Service (DDoS) Attack
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic from multiple sources. The goal is to render the system unavailable to legitimate users, often causing significant downtime and loss of access to crucial services. These attacks are executed using a large network of compromised devices, called botnets, which are controlled remotely by the attacker.
DDoS attacks are difficult to mitigate because the traffic originates from multiple sources, making it harder to distinguish between legitimate and malicious requests. As internet services have become increasingly vital to business operations, such attacks pose serious risks, causing operational disruptions, financial losses, and reputational damage.
DDoS attacks represent a significant cybersecurity threat across various industries. In sectors like banking and finance, a successful attack can halt online transactions, erode customer trust, and even lead to legal repercussions. For e-commerce platforms, continuous availability is critical, and prolonged downtime can lead to lost revenue and customer dissatisfaction. In healthcare, such attacks could potentially block access to critical systems, delaying patient care and endangering lives. Governments and utilities that rely on networked infrastructure for services like power and water distribution are also vulnerable, with attacks potentially leading to widespread disruptions.
Due to their decentralized nature, DDoS attacks are particularly challenging to defend against, making cybersecurity resilience essential across industries.
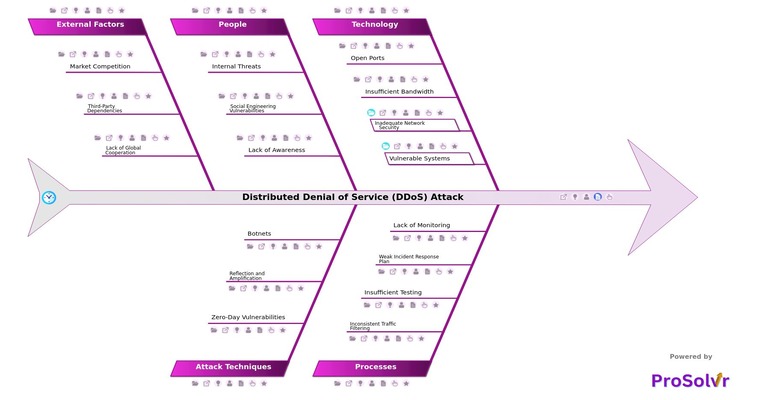
A root cause analysis (RCA) using a fishbone diagram (also known as an Ishikawa diagram) is a structured approach that helps identify the root causes of complex issues, including DDoS attacks. In the context of DDoS mitigation, a fishbone diagram can break down the problem into various categories.
By systematically analyzing these contributing factors, organizations can develop a comprehensive strategy to mitigate future risks, addressing not just the immediate symptoms but the underlying causes of the attack. This helps in both improving defensive measures and preparing for more effective responses to future threats.
Who can learn from the Distributed Denial of Service (DDoS) Attack template?
A DDoS root cause analysis template, especially when structured using tools like a fishbone diagram, can benefit several groups of people across various roles within an organization.
- Cybersecurity Teams: These professionals are directly responsible for defending against cyber threats like DDoS attacks. The template helps them systematically investigate the root causes of an attack, allowing them to strengthen their defensive measures, improve threat detection systems, and plan for future attacks.
- IT Infrastructure and Network Engineers: These teams manage the network architecture and infrastructure. Understanding the root causes of a DDoS attack enables them to identify weak points in the system, optimize network configurations, and improve traffic filtering mechanisms to enhance overall resilience.
- Incident Response Teams: Responsible for responding to and mitigating the impact of cyberattacks, these teams benefit from using the RCA template to develop faster and more effective responses. They can analyze past incidents to refine playbooks, escalation procedures, and communication strategies during future DDoS events.
- Executive Leadership and Risk Management: Executives and risk managers need to understand the business impact of DDoS attacks and how best to allocate resources to mitigate such risks. RCA templates offer them insights into operational vulnerabilities and potential financial, reputational, and legal risks.
- Compliance and Audit Teams: These teams ensure that the organization adheres to industry regulations and security standards. The findings from a DDoS RCA can inform compliance checks, ensure adherence to cybersecurity frameworks, and provide evidence of corrective actions taken to meet regulatory requirements.
- Third-Party Vendors and Service Providers: Organizations often rely on external vendors for network services, cloud infrastructure, or cybersecurity solutions. A detailed RCA of DDoS incidents helps these vendors understand their role in system failures, allowing them to improve the services they provide and enhance their security protocols in collaboration with the client organization.
Why use this template?
Using Generative AI for Root Cause Analysis (RCA) in addressing Distributed Denial of Service (DDoS) problems can significantly enhance the speed and accuracy of investigations. A quality tool like ProSolvr, can process vast amounts of data from identifying correlations and potential causes that might be missed through traditional manual analysis. AI can assist in automating the creation of fishbone diagrams, helping to organize complex information into actionable steps. This not only accelerates the identification of root causes but also aids in the development of more effective and proactive defenses against future DDoS attacks.
Use ProSolvr by smartQED to analyze the problems related to cybersecurity in your organization for effective resolution.