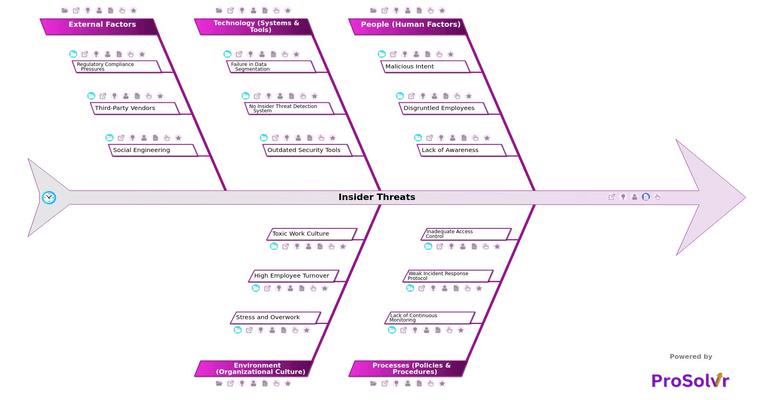
RCA of Insider Threats
Insider Threats refers to risks posed by individuals within an organization, such as employees, contractors, or business partners, who have access to sensitive information and systems. These threats can be intentional, such as a disgruntled employee stealing data, or unintentional, like an employee unknowingly falling victim to phishing attacks.
Insider threats can lead to severe consequences, including data breaches, financial loss, reputational damage, and legal consequences. Since insiders already have legitimate access, their actions can be harder to detect than external cyberattacks, making these threats particularly dangerous. The impact can be significant and wide-reaching. Financial losses are often substantial due to theft of intellectual property, sensitive data, or even sabotage of critical systems. Organizations may face operational disruptions, regulatory penalties, and a loss of trust from clients and stakeholders.
In industries such as healthcare or finance, the leakage of personally identifiable information (PII) or financial data can result in stringent legal repercussions. Insider threats, if not adequately addressed, can erode the foundation of cybersecurity protocols and leave organizations vulnerable to further exploitation.
Root Cause Analysis (RCA), using a fishbone diagram, can play a crucial role in addressing insider threats. By identifying the underlying factors that lead to such incidents—whether they are related to weak security policies, lack of employee training, or ineffective monitoring systems—organizations can implement targeted corrective actions. Gen-AI powered RCA with an application like ProSolvr can help organizations in determining how and why an insider threat occurred. Based on the findings, organizations can come up with solutions regarding what can be done to prevent similar incidents in future.
Who can learn from the Insider Threats template?
- IT and Cybersecurity Teams: These professionals are directly responsible for securing an organization’s digital infrastructure. Learning from RCA templates helps them understand how insider threats manifest, identify vulnerabilities in the current systems, and implement stronger technical controls.
- Human Resources (HR): HR plays a crucial role in understanding the behavioral and psychological aspects of insider threats. RCA insights can guide HR in recognizing warning signs, improving employee background checks, and creating programs that foster employee loyalty and cybersecurity awareness.
- Management and Executives: Leaders need to be aware of insider threats and their potential impact on business operations. An RCA template helps them understand the importance of implementing strategic policies and allocating resources to mitigate these threats proactively.
- Legal and Compliance Teams: Insider threats often have legal implications, especially regarding data breaches and regulatory violations. RCA templates help legal teams understand the circumstances leading to insider threats, ensuring compliance with relevant laws and regulations, and minimizing liability.
- Risk Management Professionals: These individuals are tasked with identifying and mitigating organizational risks. Learning from insider threats RCA allows them to incorporate cybersecurity risks into their overall risk management framework and develop comprehensive risk mitigation strategies.
- Training and Development Teams: Employee awareness and behavior are critical in preventing insider threats. RCA templates provide valuable insights that training teams can use to develop targeted cybersecurity awareness programs, ensuring all employees are educated on best practices and red flags.
Why use this template?
Using Generative AI (Gen AI) for Root Cause Analysis (RCA) of insider threats in cyber attacks offers significant benefits. An application like ProSolvr, that uses Gen AI, can quickly analyze vast amounts of information that may not be possible for human analysts. It helps in pinpointing the root causes of insider incidents more efficiently. Authorities can gain insights, suggest preventive measures and enhance the overall security by continuously learning from new data and evolving threats.
Use ProSolvr by smartQED to identify potential threats in your company and deploy suitable corrective actions to mitigate threats in future.