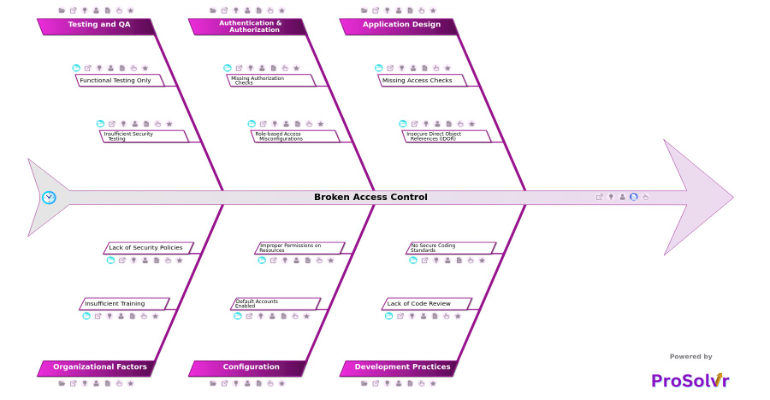
RCA of Broken Access Control
Broken Access Control is one of the most critical vulnerabilities in modern web applications and enterprise systems. It occurs when users are able to act outside of their intended permissions, accessing or modifying data, functions, or resources that should be restricted. Common forms of this issue include missing authorization checks, insecure direct object references (IDOR), and misconfigured user roles. These lapses in access control create severe risks such as data leaks, privilege escalation, and unauthorized system manipulation. They can stem from poor development practices like lack of code reviews, absence of secure coding standards, and inadequate authentication/authorization mechanisms.
When an application exposes object identifiers in URLs without validating user permissions, it allows attackers to manipulate those identifiers and gain unauthorized access to sensitive data. Similarly, when developers assume that the user interface alone is sufficient to restrict access, they overlook the necessity of enforcing security at the server or backend level leading to major breaches.
Again, when developers are unaware of security risks due to no secure coding guidelines, or when endpoints fail to enforce user roles, systems become vulnerable. Even operational oversights like default credentials remaining unchanged or permissions set too broadly on sensitive files can expose organizations to cybersecurity incidents.
Once such an incident occurs, conducting a structured root cause analysis becomes essential not only to understand what went wrong, but also to prevent future occurrences. A GEN-AI powered root cause analysis using a fishbone diagram aligned with Six Sigma principles can greatly enhance the effectiveness of post-incident problem-solving. The fishbone diagram (also known as the Ishikawa diagram) categorizes root causes under clearly defined domains. The structured nature of this analysis enables teams to come up with Corrective and Preventive Actions (CAPA).
An application like ProSolvr, which leverages GEN-AI to create fishbone diagrams for root cause analysis, can significantly accelerate and enrich this process. By allowing users to input known causes, ProSolvr generates a structured analysis that guides teams through cause categorization and prioritization.
Who can learn from the Broken Access Control template?
- Developers: Developers can learn the importance of implementing secure coding practices and not relying solely on the user interface for access control. Understanding how issues arise can help them write more secure backend logic.
- QA/Testers: Quality Assurance professionals can recognize the need to incorporate security testing into their functional test plans. By identifying gaps, they can advocate for penetration testing and security validation in the QA cycle.
- System Administrators: System admins can understand the various kinds of risks. The RCA teaches them to review and harden configurations regularly to prevent unauthorized access.
- Security Teams: Security analysts can use the RCA to refine threat models and improve access control policies. It also emphasizes the importance of auditing endpoints and role assignments to catch vulnerabilities.
- Project Managers: Project managers can see how organizational gaps contribute to technical vulnerabilities. This insight can guide them to allocate resources for security training and enforce secure development standards in project planning.
- Compliance Officers: Compliance teams can use the RCA to ensure that access control measures align with regulatory standards. Understanding failures helps them enforce least-privilege principles and better audit access control practices.
Why use this template?
ProSolvr's visual representation aids in stakeholder communication, ensuring that every identified cause leads to a documented corrective or preventive measure. This kind of AI-powered root cause application not only clarifies the pathways of failure but also helps organizations institutionalize better access control practices, ultimately reducing the risk of repeat incidents. By visually mapping out the contributing factors under each category, teams can pinpoint the exact breakdowns that led to the vulnerability.
Use ProSolvr by smartQED to effectively resolve problems in your organization.